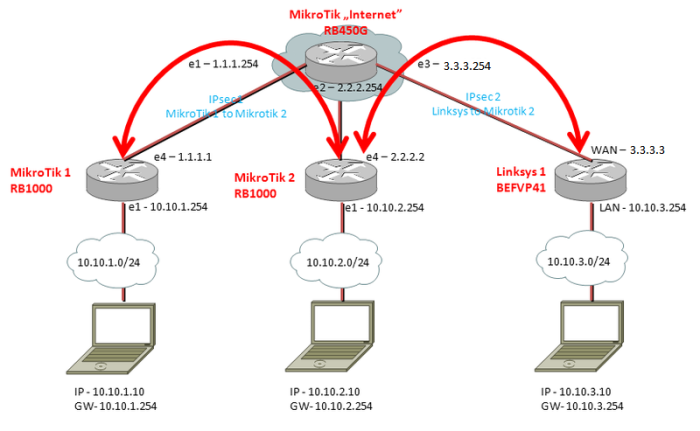
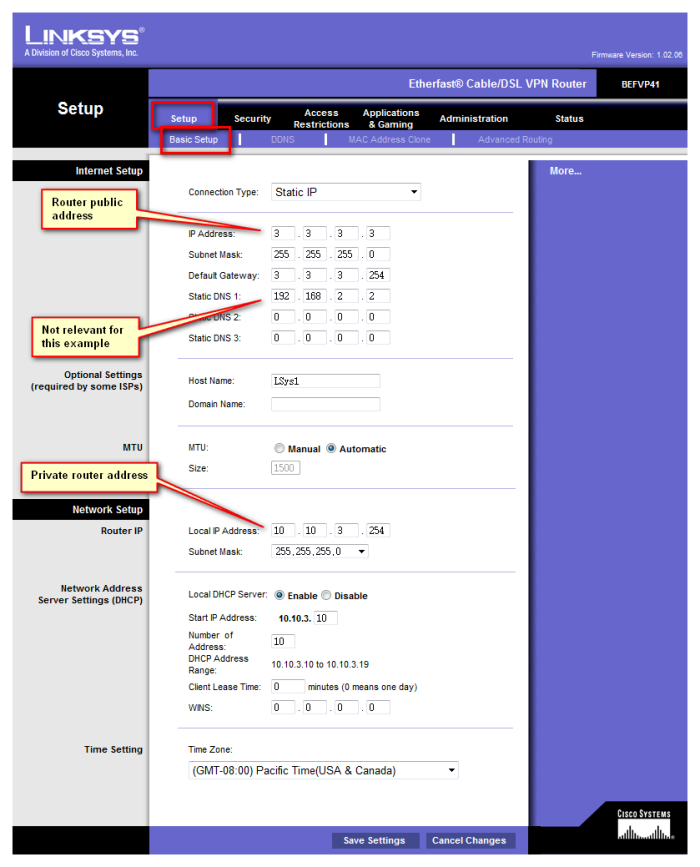
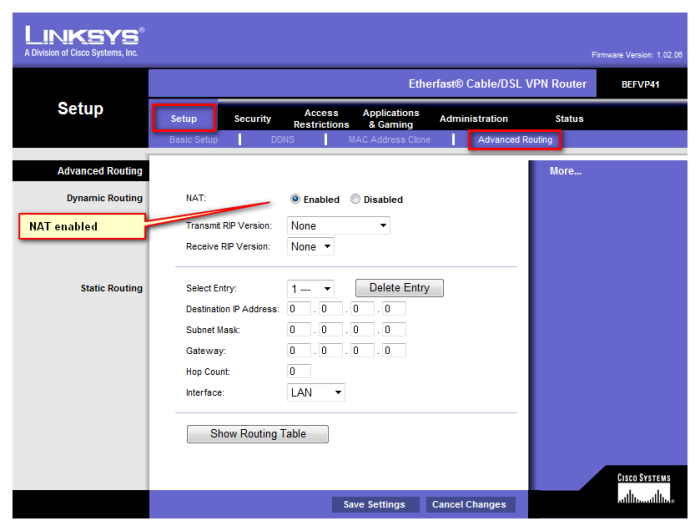
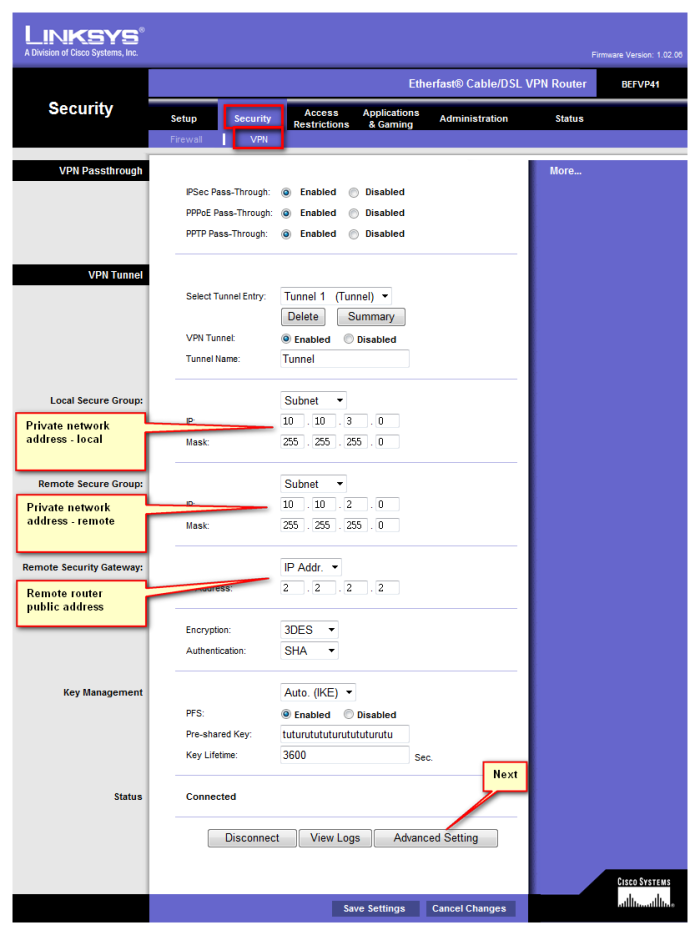
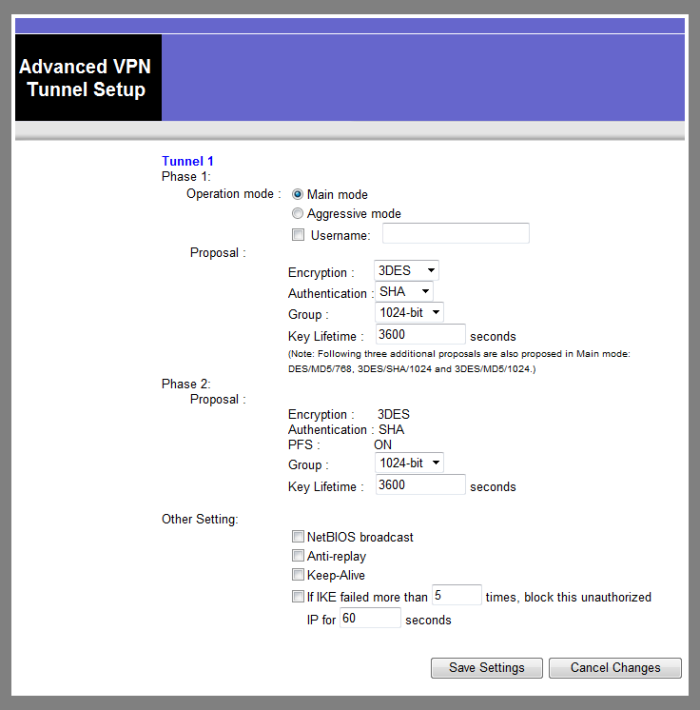
IPsec tunnel [Mikrotik to Linksys BEFVP41][Mikrotik to Mikrotik]
Check the differences between IPsec tunnel and IPsec transport.
http://wiki.mikrotik.com/wiki/IPSec_VPN_/_Mikrotik_and_Linksys_BEFVP41
Assumptions:
| First location | Mikrotik RB1000 | Second location | Mikrotik RB1000 | Third location | Linksys BEFVP41 | ||
|---|---|---|---|---|---|---|---|
| Private network address | 10.10.1.0/24 | Private network address | 10.10.2.0/24 | Private network address | 10.10.3.0/24 | ||
| Private interface address | 10.10.1.254 | Private interface address | 10.10.2.254 | Private interface address | 10.10.3.254 | ||
| Public interface address | 1.1.1.1 | Public interface address | 2.2.2.2 | Public interface address | 3.3.3.3 | ||
| IPsec secret | 12345678 | IPsec secret | 12345678 | IPsec secret | 12345678 |
Internet router RB450 is faking Internet connection and does the basic routing between public networks 1.1.1.0, 2.2.2.0 and 3.3.3.0. NAT is configured on all routers and they also provide DHCP for respective networks.
Internet router configuration
/ip address add address=1.1.1.254/24 disabled=no interface=ether1 network=1.1.1.0 add address=2.2.2.254/24 disabled=no interface=ether2 network=2.2.2.0 add address=3.3.3.254/24 disabled=no interface=ether3 network=3.3.3.0
First router configuration
1.IP addressess
/ip address add address=10.10.1.254/24 disabled=no interface=ether1 network=10.10.1.0 add address=1.1.1.1/24 disabled=no interface=ether4 network=1.1.1.0
2.Default route
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=1.1.1.254 scope=30 \
target-scope=10
3.NAT - Note that NAT bypass for IPsec tunnels rule is on the top of the list !!! It is set for all 10.10.x.x networks but you can specify subnets individually.
/ip firewall nat add action=accept chain=srcnat disabled=no dst-address=10.10.0.0/16 src-address=\ 10.10.1.0/24 add action=masquerade chain=srcnat disabled=no out-interface=ether4
4.IPsec
/ip ipsec proposal set default auth-algorithms=sha1 disabled=no enc-algorithms=3des lifetime=30m name=\ default pfs-group=modp1024 /ip ipsec peer add address=2.2.2.2/32 auth-method=pre-shared-key dh-group=modp1024 disabled=no \ dpd-interval=2m dpd-maximum-failures=5 enc-algorithm=3des exchange-mode=main \ generate-policy=no hash-algorithm=md5 lifebytes=0 lifetime=1d my-id-user-fqdn=\ "" nat-traversal=yes port=500 proposal-check=obey secret=!secret! \ send-initial-contact=yes /ip ipsec policy add action=encrypt disabled=no dst-address=10.10.2.0/24 dst-port=any \ ipsec-protocols=esp level=require priority=0 proposal=default protocol=all \ sa-dst-address=2.2.2.2 sa-src-address=1.1.1.1 src-address=10.10.1.0/24 \ src-port=any tunnel=yes
Second router configuration
1.IP address
/ip address add address=10.10.2.254/24 disabled=no interface=ether1 network=10.10.2.0 add address=2.2.2.2/24 disabled=no interface=ether4 network=2.2.2.0
2.Default route
/ip route add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=2.2.2.254 scope=30 \ target-scope=10
3.Note that NAT bypass for IPsec tunnels rule is on the top of the list !!! It is set for all 10.10.x.x networks but you can specify subnets individually.
/ip firewall nat add action=accept chain=srcnat disabled=no dst-address=10.10.0.0/16 src-address=\ 10.10.2.0/24 add action=masquerade chain=srcnat disabled=no out-interface=ether4
4.IPsec
/ip ipsec proposal set default auth-algorithms=sha1 disabled=no enc-algorithms=3des lifetime=30m \ name=default pfs-group=modp1024
4.1.First tunnel - to Mikrotik router at 1.1.1.1
/ip ipsec peer add address=1.1.1.1/32 auth-method=pre-shared-key dh-group=modp1024 disabled=no \ dpd-interval=2m dpd-maximum-failures=5 enc-algorithm=3des exchange-mode=main \ generate-policy=no hash-algorithm=md5 lifebytes=0 lifetime=1d \ my-id-user-fqdn="" nat-traversal=yes port=500 proposal-check=obey secret=\ !secret! send-initial-contact=yes
4.2.Second tunnel - to Linksys router at 3.3.3.3
/ip ipsec peer add address=3.3.3.3/32 auth-method=pre-shared-key dh-group=modp1024 disabled=no \ dpd-interval=2m dpd-maximum-failures=5 enc-algorithm=3des exchange-mode=main \ generate-policy=no hash-algorithm=md5 lifebytes=0 lifetime=1d \ my-id-user-fqdn="" nat-traversal=yes port=500 proposal-check=obey secret=\ !secret! send-initial-contact=yes
4.3. IPsec policy
/ip ipsec policy add action=encrypt disabled=no dst-address=10.10.1.0/24 dst-port=any \ ipsec-protocols=esp level=require priority=0 proposal=default protocol=all \ sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 src-address=10.10.2.0/24 \ src-port=any tunnel=yes add action=encrypt disabled=no dst-address=10.10.3.0/24 dst-port=any \ ipsec-protocols=esp level=require priority=0 proposal=default protocol=all \ sa-dst-address=3.3.3.3 sa-src-address=2.2.2.2 src-address=10.10.2.0/24 \ src-port=any tunnel=yes add action=masquerade chain=srcnat disabled=no out-interface=ether4
5.Keep alive for Linksys router
/system scheduler add disabled=no interval=30s name="Ping remote" on-event=\ "ping 10.10.3.254 src-address=10.10.2.254 count=1" policy=\ ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api \ start-date=nov/25/2011 start-time=00:00:00
When the tunnel is dropped on Mikrotik side, Linksys is unable to bring it up again even if the “keep alive” check box is properly checked. To circumvent this bug, the simplest way is to send a single ping from Mikrotik every 30 seconds. If the tunnel was droped in the meantime, this ping will bring it up again. Be carefull what you are pinging and from which IP. Ping must be sourced from local private interface to remote private interface which can communicate only if the tunnel is established, and if it isn't, this ping will initiate it. Better way would be to engage NetWatch for this task, but problem is that you cannot specify ping source (AFAIK).